Centralizing AWS Root Account Access
Typically when I come across people, it’s quite hard to articulate what an “AWS Account actually is, and what does the root user of an AWS account do, or what is it for? This is an easier concept if you’re familiar with Linux/Unix style of hierarchy with root users, but for those less familiar it can be trickier to grasp.
What happens is that when you create an AWS account, the email address you use to create the account becomes the “root” user of that AWS account. An AWS account is an isolated container of resources and identities. We typically use these to help isolate resources or environments from each other to lower the blast radius and attack vector if an AWS account is compromised by a nefarious actor for example.
When you’re managing a multi-account AWS organization (either with AWS Organizations, manually, or with AWS Control Tower, you still end up with a bunch of AWS accounts which all have a root user and associate root user email address per AWS account. This is overhead to manage and means you must manage MFA keys etc per AWS account.
AWS now allows you to delegate root account authority to a single AWS account. This means by default it will use your Management AWS account for logical reasons. You can specify an additional delegated account other than the Management account for break-glass type reasons (although I prefer using an IAM role for this). So, one AWS account root user, one MFA key. That sounds great!
Delegating Root Access Authority
AWS now allows you to delegate root account authority to a single AWS account, the default account is your Management account. Alternatively, you can specify a different delegated account for break-glass scenarios. This streamlines management:
- One root user and one MFA key for all accounts.
- Simplifies management and improves security.
How to Centralize Root Access for Member Accounts
Follow these steps to enable centralized root access:
- Go to the IAM Dashboard > Root Access Management in the AWS Management Console.
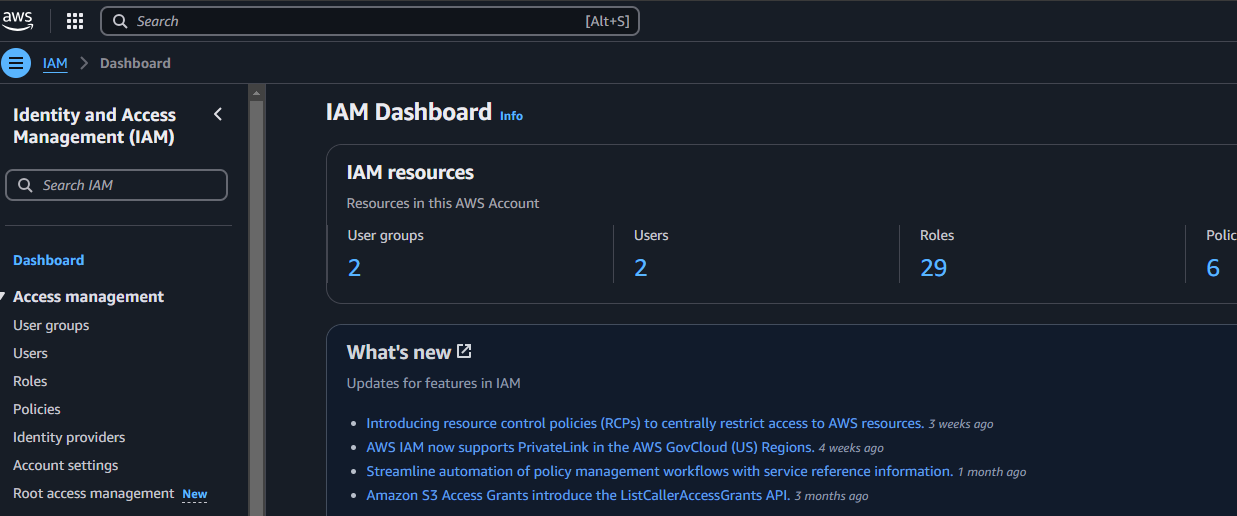
Click ‘Root access management’ and then Enable:
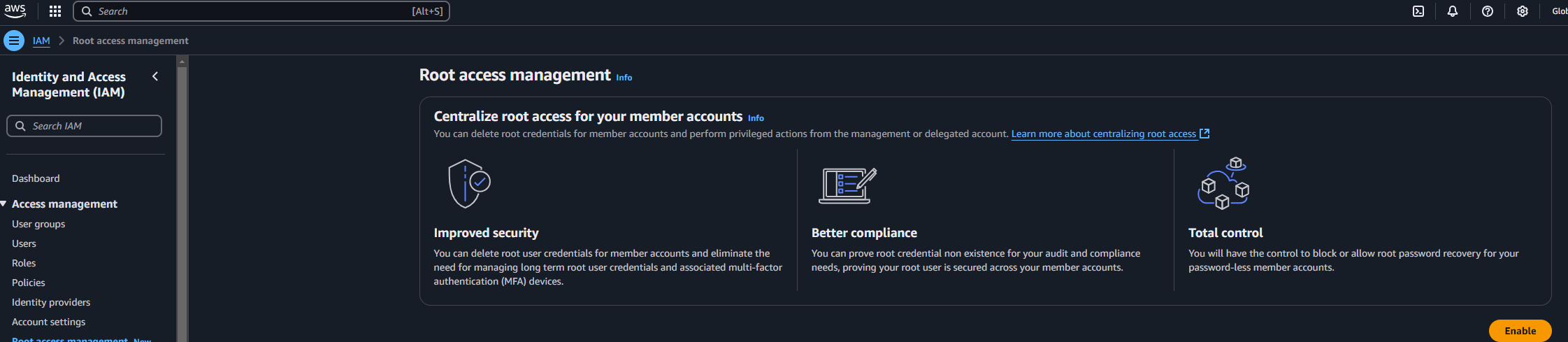
-
Select Root Credentials Management to allow your management account and delegated account to manage root credentials.
Then, select Privileged root actions in member accounts.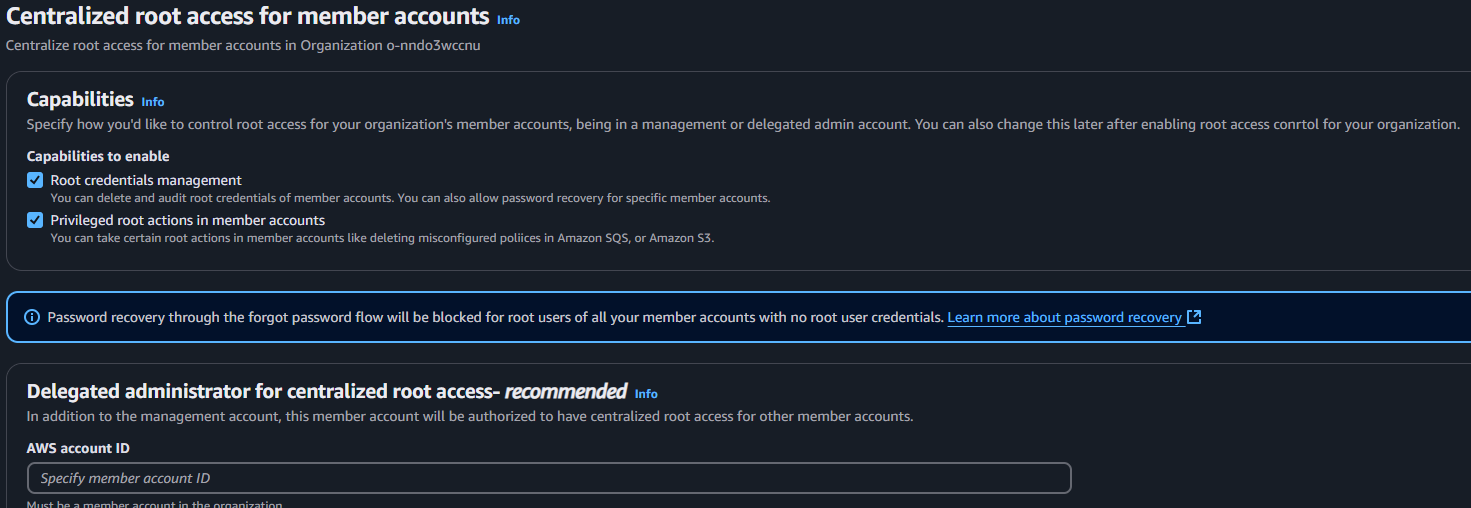
You will now see the confirmation screen:
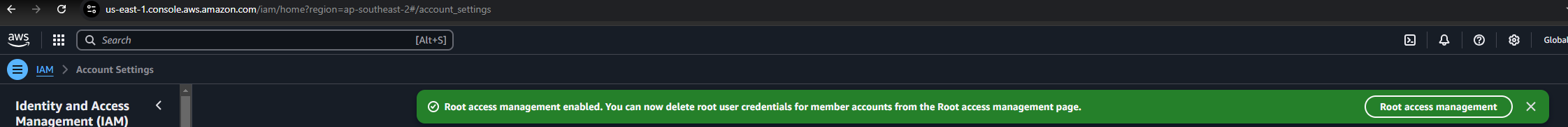
-
If you have a break-glass IAM role, leave the Optional Delegated Account field blank.
Once enabled, delete the root user credentials for the member accounts:
- Click on the account and then
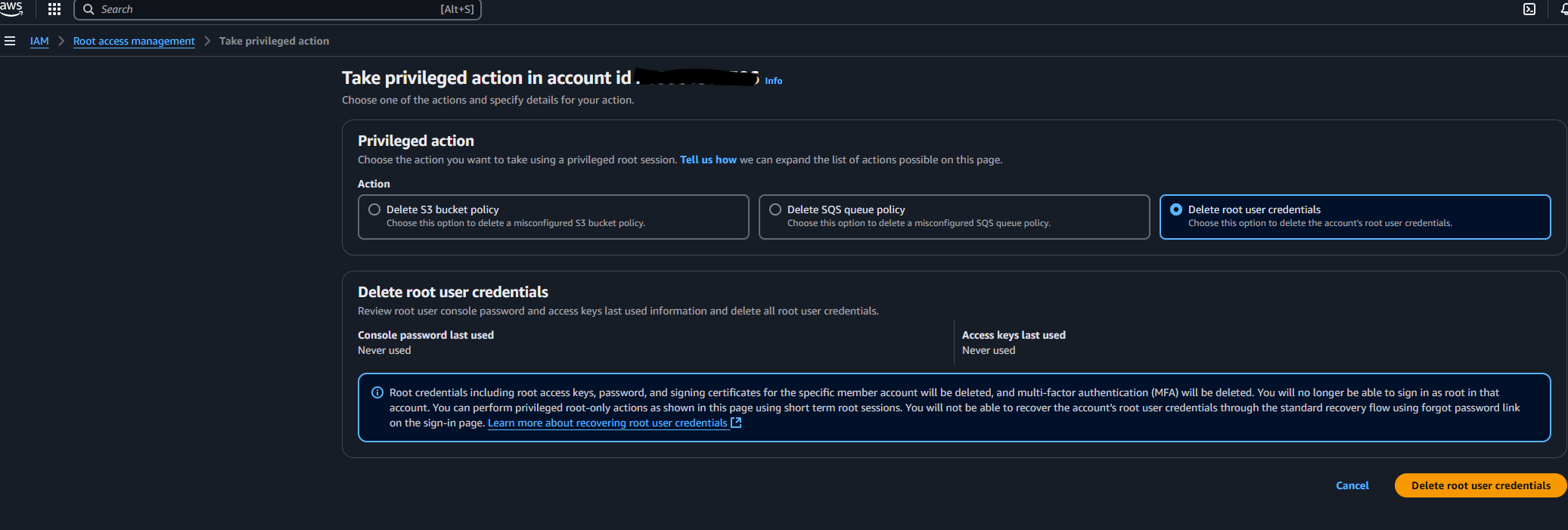
Take Privileged Actionbutton.
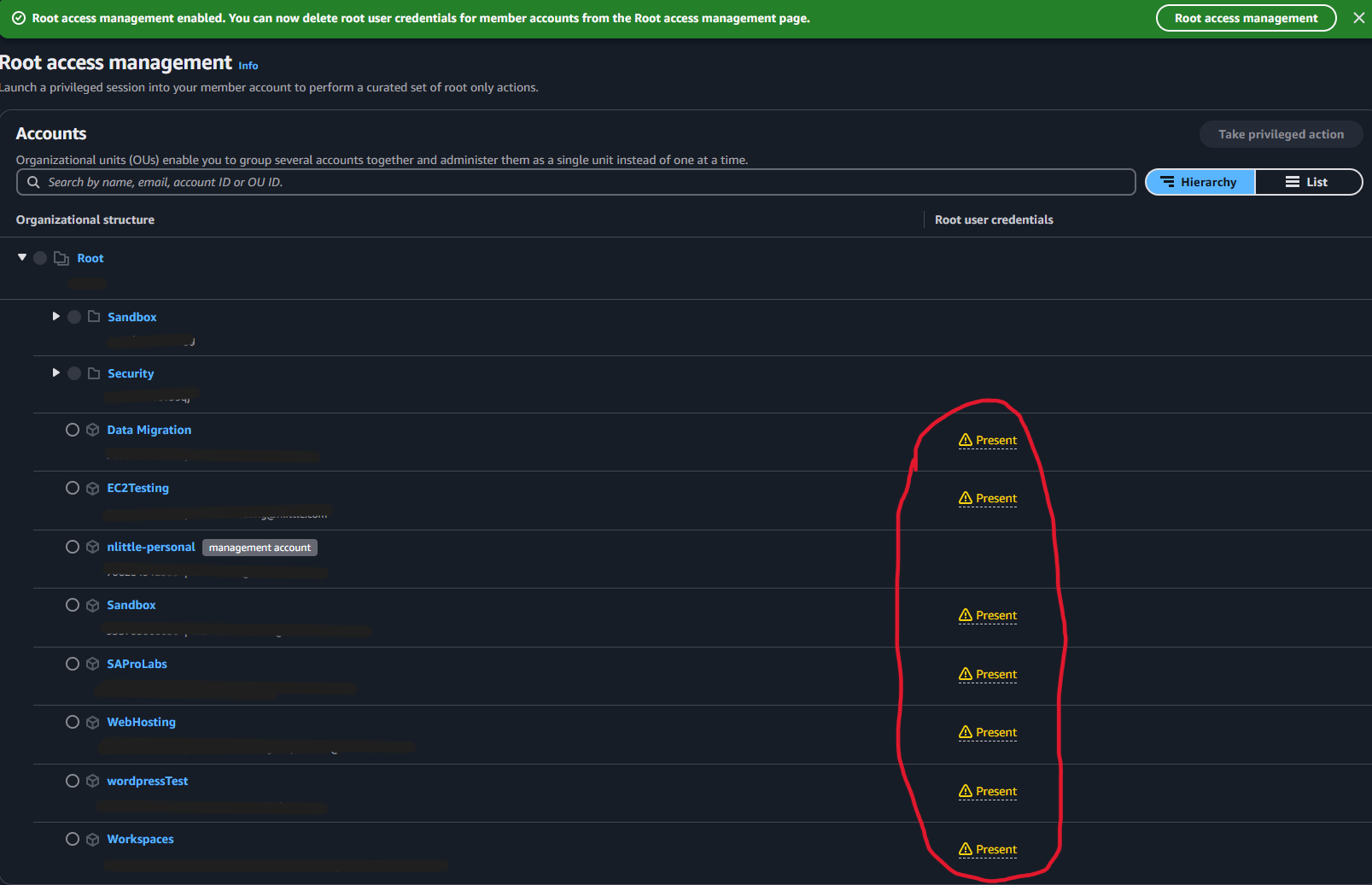
- Select
Delete Root Credentials.
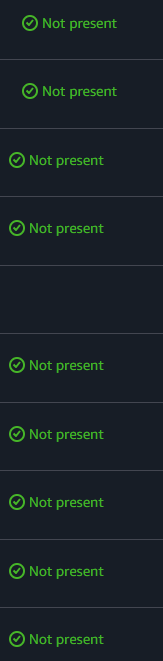
Now go through and confirm there are no longer any root credentials present:
- Click on the account and then
If you do need to recover deleted root credentials off the other AWS accounts, then AWS does support a recovery process if required. Enable account recovery of the root user:
“If you need to recover root user credentials for a member account, the Organizations management account or delegated administrator can perform the Allow password recovery privileged task. The person with access to the root user email inbox for the member account can reset the root user password to recover root user credentials. We recommend deleting root user credentials once you complete the task that requires access to the root user.”
There are some considerations such as if you use SCP’s across your organization to deny or allow actions for example. And at the time of writing your Security Hub score won’t improve by doing this sadly (as the feature is so new), so hopefully this is embedded into Security Hub in the future.
Any new AWS accounts that you create in your AWS Organization after this feature is enabled do not show as having a root account once created (so it applies to the new accounts automagically as you’d expect).
That’s it. Pretty simple, but effective!